Kerberos, Understanding Kerberos Concepts Ig Ldap Sso Auth 3 4 0 Documentation
Kerberos protocol a computer network authentication protocol to allow server communication over a non-secure network Kerberos saga a science fiction series by Mamoru Oshii Keroberos or Cerberus a character from Cardcaptor Sakura StrayDog. The Kerberos authentication protocol provides a mechanism for mutual authentication between entities before a secure network connection is established.
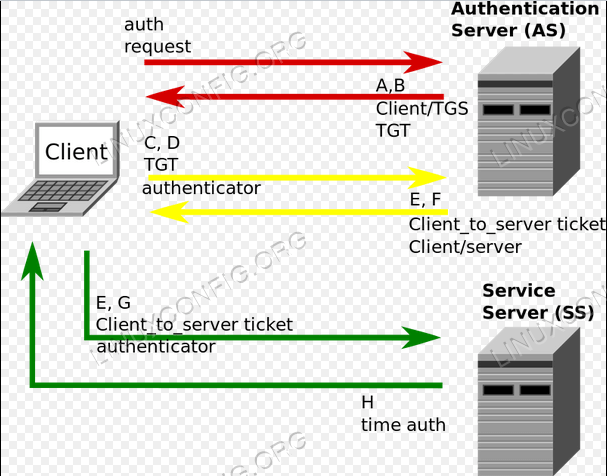
How To Install Kerberos Kdc Server And Client On Ubuntu 18 04 Linux Tutorials Learn Linux Configuration
A free implementation of this protocol is available from the Massachusetts Institute of Technology.
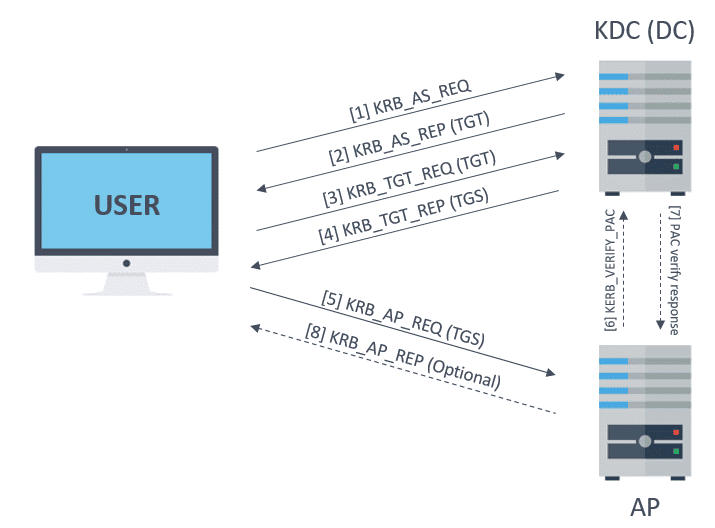
Kerberos. For Mac Kerberos is built in to Mac OS X. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. How does Kerberos work.
Primary benefits are strong encryption and single sign-on SSO. With that as its inspiration the Massachusetts Institute of Technology developed a protocol to protect its own projects in the late 1980s. In the modern world MIT Computer Scientists used the name and visual of Kerberos for.
Hes a big 3 headed dog with a snake for a tail and a really bad temper. For plugin module developers. Astronomy The 4th moon of Pluto discovered in 2011.
It uses secret-key cryptography and a trusted third party for authenticating client. According to Greek mythology Kerberos Cerberus was the gigantic three-headed dog that guards the gates of the underworld to prevent the dead from leaving. Kerberos is a network authentication protocol.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Throughout this documentation the two entities are called the client and the server even though secure network connections can be made between servers. MIT Kerberos for Windows KfW is an integrated Kerberos release for Microsoft Windows operating systems.
In Kerberos Authentication server and database is used for client authentication. This topic contains information about Kerberos authentication in Windows Server 2012 and Windows 8. Kerberos Alternative spelling of Cerberus An authentication protocol using a central ticket server.
Kerberos is available in many commercial products as well. Kerberos Panzer Cops a film by Mamoru Oshii. It is designed at MIT to allow network resources in a secure manner.
According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld. Kerberos is a network authentication protocol. KfW is a software application that installs tickets on a computer in order to grant access to essential MIT services.
Kerberos is built in to all major operating systems including Microsoft Windows Apple OS X FreeBSD and Linux. Kerberos is available in many commercial products as well. How to build this documentation from the source.
For Windows a utility called Network Identity Manager provides the graphical user interface for managing Kerberos functions. Kerberos is an authentication protocol enabling systems and users to prove their identity through a trusted third-party. Contributing to the MIT Kerberos Documentation.
Kerberos is the mythological three-headed Greek creature which is guarding the gates of underworld to prevent souls from escaping. Kerberos is a network authentication protocol developed by the Massachusetts Institute of Technology MIT. Kerberos is an authentication protocol that is used to verify the identity of a user or host.
Kerberos provides secure authentication for various services at Stanford such as Stanford OpenAFS. Kerberos runs as a third-party trusted server. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography.
The Kerberos protocol uses secret-key cryptography to provide secure communications over a non-secure network. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. The protocol was initially developed at the Massachusetts Institute of Technology MIT as part of a larger project called Project Athena.
Protocols and file formats. Kerberos is a computer network authentication protocol. Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network such as the internet.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. In this article we will see discussed the Kerberos concept and its working with the help of an example.
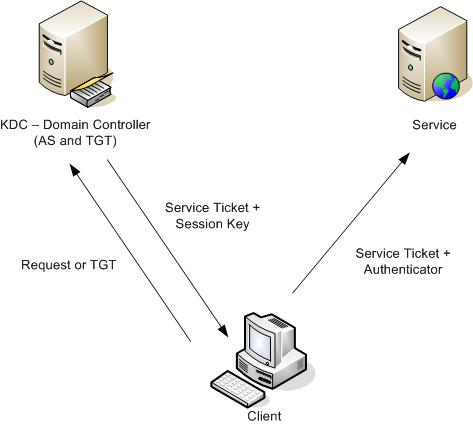
Kerberos Szenarios Data Warehousing Bissantz Company
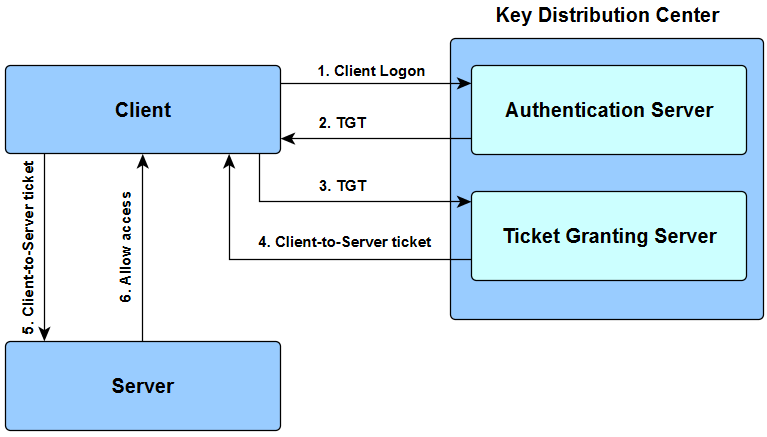
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security

Windows Event Id 4768 A Kerberos Authentication Ticket Was Requested Adaudit Plus
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community

Wie Funktioniert Die Kerberos Authentifizierung
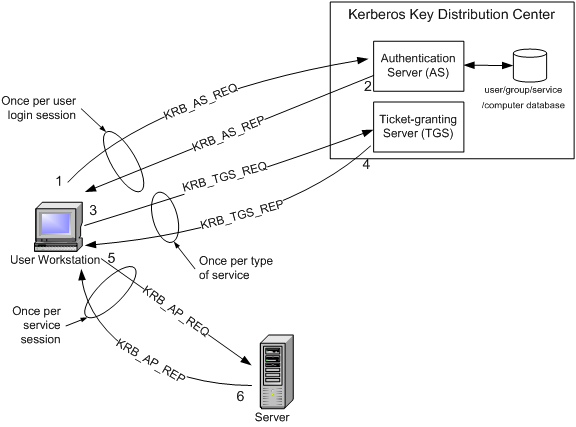
Intel Amt Sdk Implementation And Reference Guide

Kerberos I How Does Kerberos Work Theory

Azure Atp Golden Ticket Attack Understanding Kerberos It Pirate
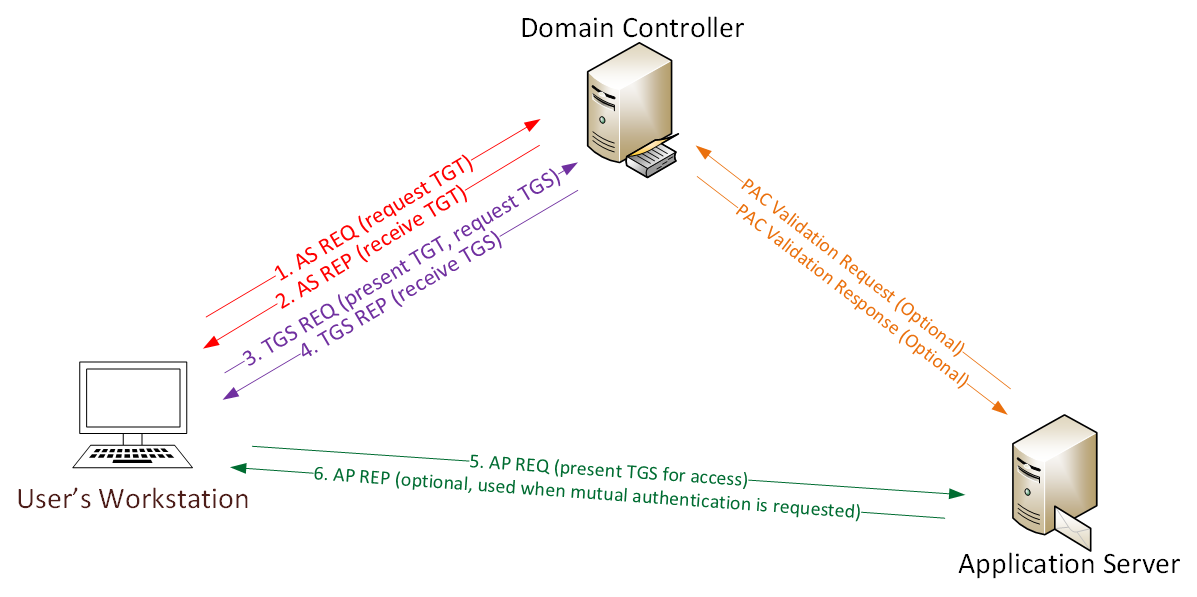
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security
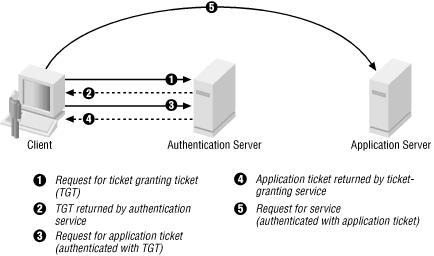
Understanding Kerberos Concepts Ig Ldap Sso Auth 3 4 0 Documentation

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
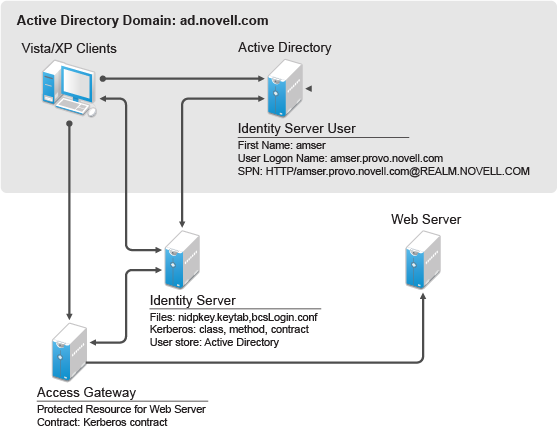
Kerberos Authentication Netiq Access Manager Appliance 4 5 Administration Guide

Introduction Kerberos For Beginners Intro To Network Authentication Protocol

Kerberos Operation Zeroshell Linux Router

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram

Taming The Beast Kerberos For The Sql Server Dba Youtube
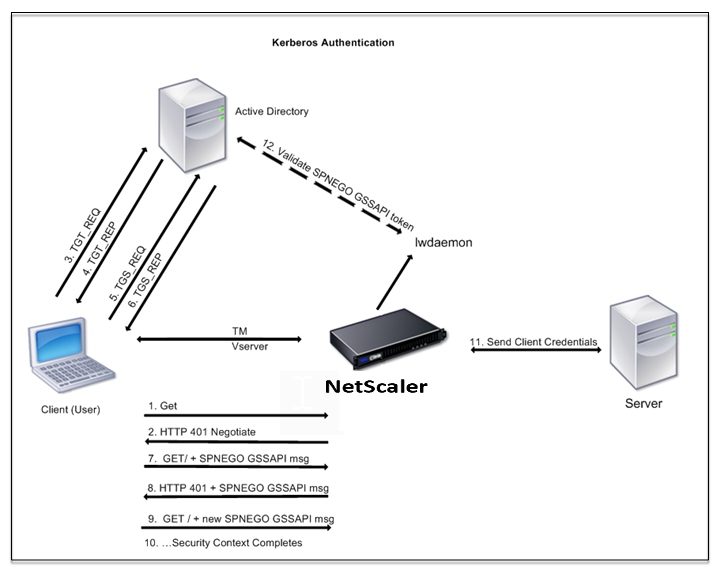
How Citrix Adc Implements Kerberos For Client Authentication




Post a Comment
Post a Comment